Corporate Security Management – Securing Corporate Assets Efficiently and Effectively
What you can expect
- How can corporate security management be set up efficiently?
- How can the integration along the 2nd line of defense succeed?
- How is the technical implementation carried out at the strategic and operational level?

About the author
Erik Guschlbauer is Product Manager for ADOGRC and Service & Innovation Manager at BOC Group.
The term corporate security encompasses the physical security of corporate assets, the occupational safety of employees, information security, and also emergency and crisis management. The area of responsibility here covers a broad spectrum of hazards and risks with varying probabilities and effects, as well as the management of situations that threaten the existence of the company. A close cooperation between security management and the management systems along the 2nd Line of Defence is essential in order to learn as soon as possible about negative developments in the organization. In this article, we show how to set up your corporate security management in an efficient and integrated way.
Introduction
Capabilities are created through a combination of staff members, processes, technology and information. Enterprise security encompasses the capabilities that an enterprise must proactively manage to ensure continued existence and progress, such as:
- Safeguarding of corporate assets
- Security of information and data
- Safeguarding of jobs and employees
- Planning ahead for possible emergencies and crises
- Measures to prevent and investigate crime and fraud
- Safeguarding the environment and other assets
Corporate security management deals with all organizational measures and means for the systematic identification, analysis, evaluation and control of security-relevant aspects, such as maintaining the confidentiality of information and access restrictions to assets that require protection.
The structure of safety management, like all other governance systems, is divided into the following 3 levels:
- Governance
- Strategy
- Operational implementation
In line with the 3 Lines of Defence model, the tasks relating to governance and strategy are the responsibility of a company’s security function (2nd Line of Defence). The operational implementation is the responsibility of the managers in the organization’s specialist departments (1st Line of Defence). The internal audit department (3rd Line of Defence) is responsible for monitoring and checking the appropriateness and effectiveness of the system.
Governance
The governance activities of security management include the normative specification of the management system and the definition of its goal and purpose. Norms, standards and frameworks for corporate security management help to proactively and systematically address increased security needs. These include:
- Archimate
- COSO
- ISM3
- ISO 22301
- ISO 27000
- ISO 27001
- ISO 31000
- ITIL
- ÖNORM S 2400
- TOGAF
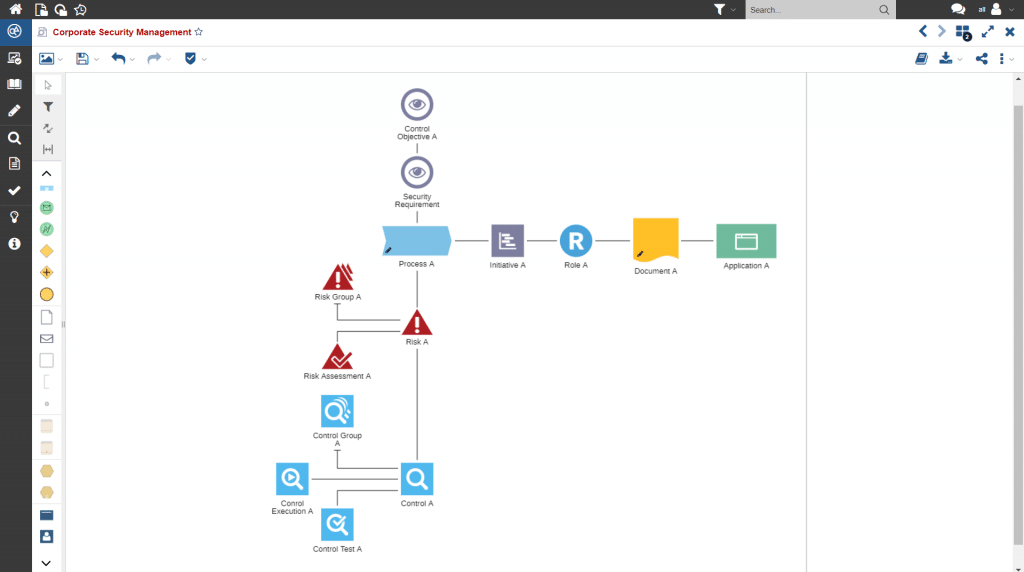
The scope of the management system is determined by the individual company requirements. Based on the defined criteria, the relevant assets are identified. This is done starting from the process map, as the processes refer to specifications, norms and standards and directly show which IT systems, roles and documents are relevant. BOC Group’s GRC suite – ADOGRC – offers a range of preconfigured views and analyses to support you in all these tasks.
Figure 1: Dependency analysis of a business-critical process to its assets with reference to risks and control measures in the GRC suite ADOGRC.
Security management is not a one-time activity. It is about managing an operational system that dynamically evolves itself as well as its contents and whose active design requires dedicated specifications for planning, implementation, monitoring as well as improvements.
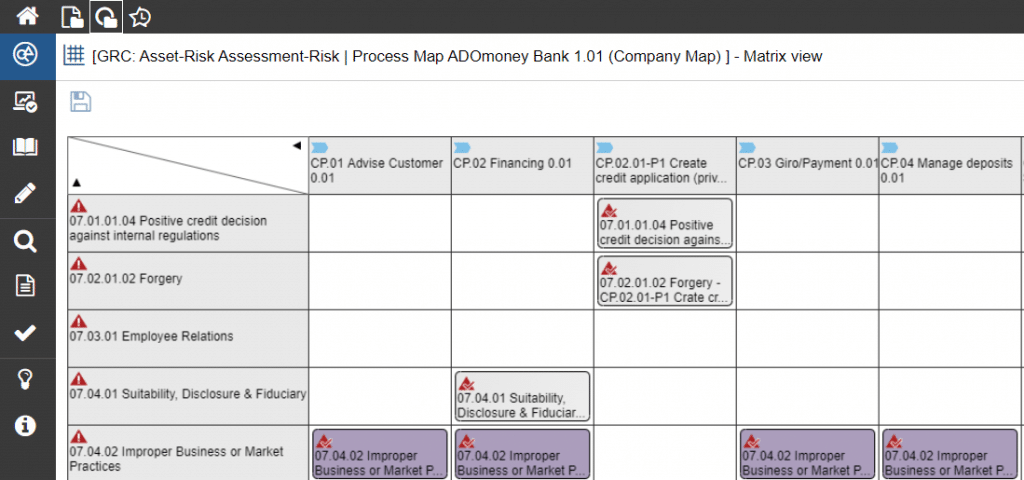
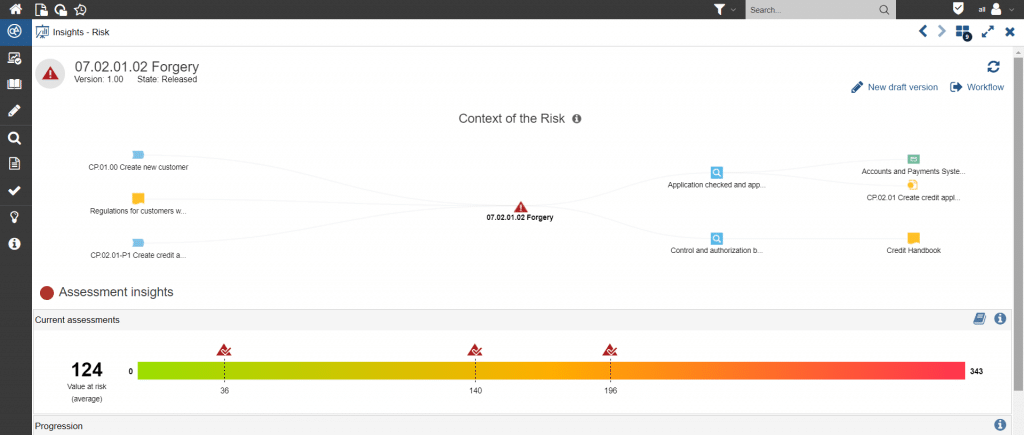
Since corporate security management is introduced into the company according to the “top-down” principle, it is essential to secure the “buy-in” of management in advance by demonstrating its necessity and added value. For this purpose, ADOGRC can be used to perform an analysis of the affected, security-relevant assets and their current risk assessment (including the need for action).
Figure 2: Matrix of critical assets and their risk assessment in ADOGRC.
A policy summarizes the terms, the scope and the integration of safety management into the integrated management system. When creating the policy, other management systems must also be mentioned, such as risk management, ICS or compliance management. This is essential, as all these disciplines are related to risks, controls and measures, and a common understanding of these is essential for integration along the Three Lines of Defence. Otherwise, there is a risk that the disciplines will talk past each other.
Strategy
Those responsible for strategy must develop the specifications and, in doing so, design them in such a way that implementation can be carried out as effectively and efficiently as possible by the operational units.
The tasks of strategic security management include planning, providing the necessary organizational and technical structures, ongoing support for the operating units, continuous monitoring of implementation, evaluation and improvement, and regular reporting. ADOGRC also offers extensive options for those responsible for strategy and their activities.
Planning
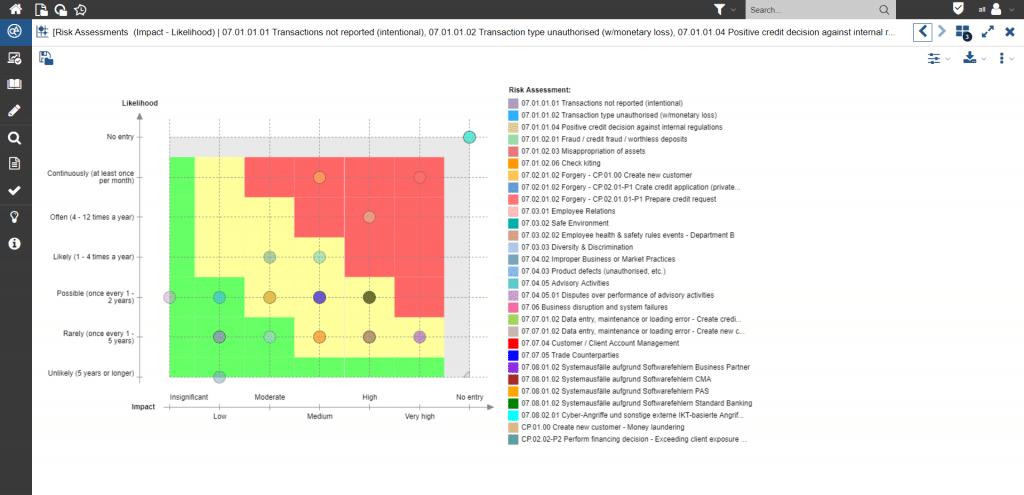
Efficient security management is based on risks. Only when possible threats are known we can protect against them. In order to deploy the available resources according to the criticality of the risks, we can fall back on the assessment of the relevant risks. However, such a uniform, continuous and accurate assessment of security risks must always be seen in the overall context of other types of risks. This is why the harmonization of governance systems is of such high importance in order to provide a uniform and integrated view of all risks of the different governance systems.
Figure 3: FMEA matrix for visualization of the scales in ADOGRC
Figure 4: Visualization of the next planned implementation dates in ADOGRC
Monitoring implementation
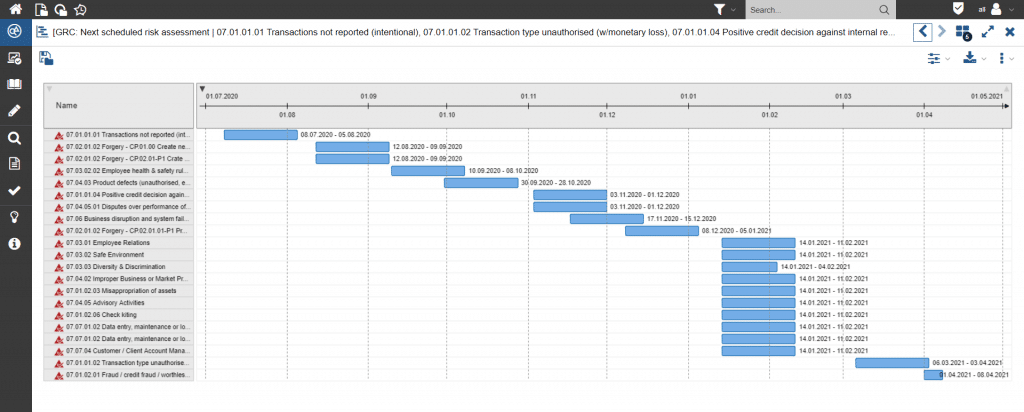
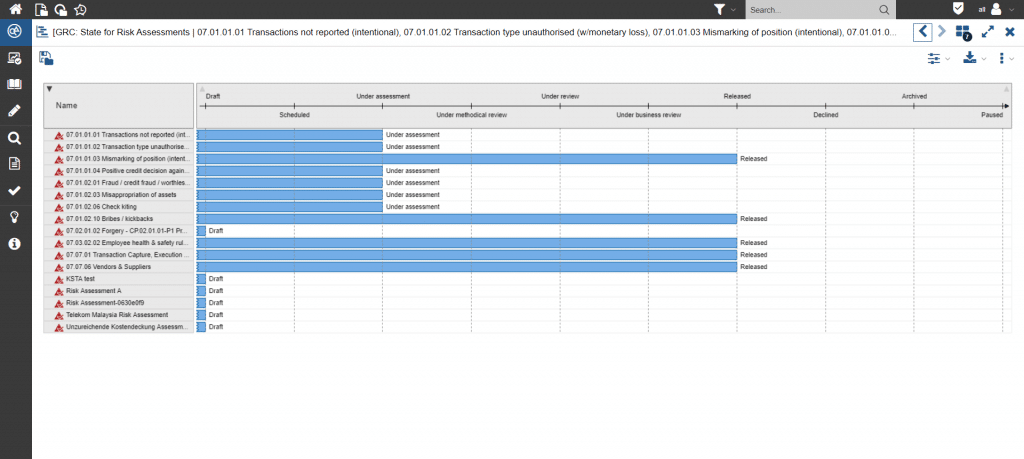
The implementation of safety management in the individual departments presents companies with a major challenge, as the assessment has to be carried out decentrally by the experts within defined timeframes. In order to obtain control-relevant information, it is necessary to track the development of the relevant risks and to monitor the quality and consistency of the assessment.
Thanks to the close integration within the integrated management system, established workflows, scales and structures can be applied and historical data used for evaluation.
Figure 5: GANTT chart showing risk assessment status in ADOGRC
Figure 6: Detail dashboard with gradients in ADOGRC
Evaluation and improvement
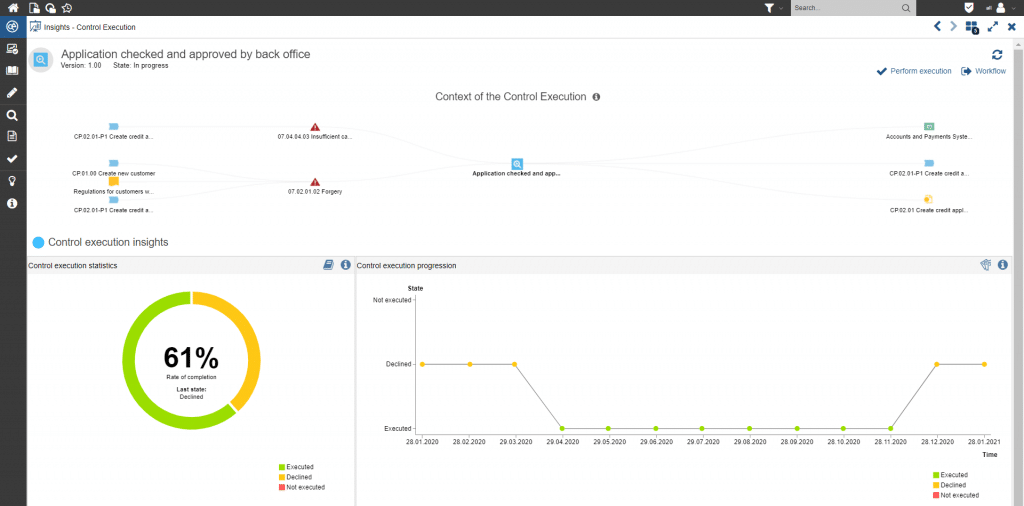
You can’t control what you can’t measure. And you can’t improve what you can’t control. Continuous records, transparency and consistency across governance systems are therefore critical factors in improving the security landscape. Based on the risk assessment, measures are derived and appropriate controls are established. In Corporate Security Management, the controls and measures are reviewed with regard to their status and effectiveness.
Figure 7: Measures/Controls Dashboard in ADOGRC
Reporting and analysis
All development-relevant work steps are automatically documented by the security system. In addition to traceability, this allows the generation of ad-hoc evaluations and analyses. The data can be evaluated directly within the application or transferred to specialized solutions via standardized interfaces, for example to support internal auditing or auditors.
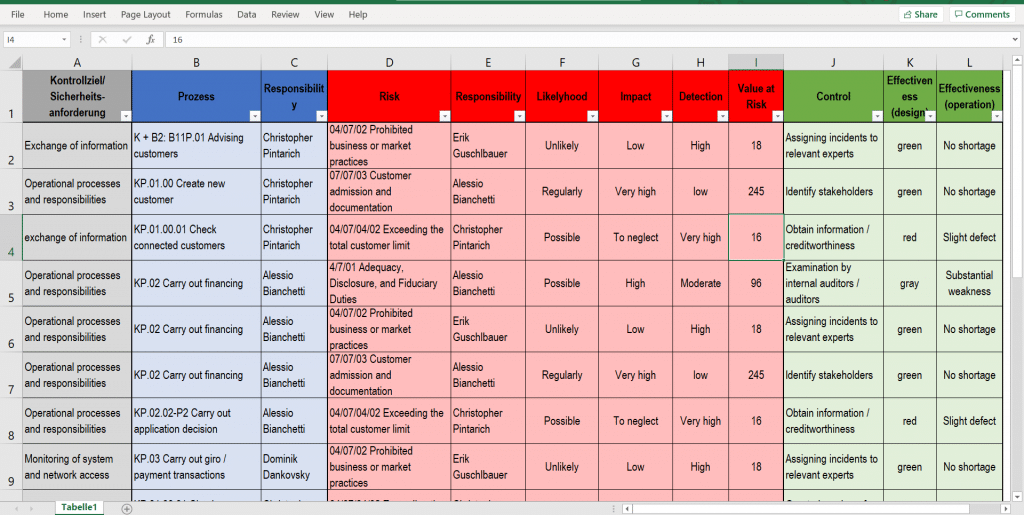
Figure 8: Risk-control matrix based on business processes in ADOGRC
Operational implementation by the departments
It is the responsibility of the business units to identify the relevant assets on the basis of the specifications and to provide a risk assessment. In addition to assigning a unique owner, the definition of the assessment context (e.g., loss events that have occurred, current threats, lifecycle of the assets, etc.) is essential. Information and details about the assessment and the required work steps are provided and tracked automatically and personalized by a governance system like ADOGRC, which enables an efficient task fulfillment.
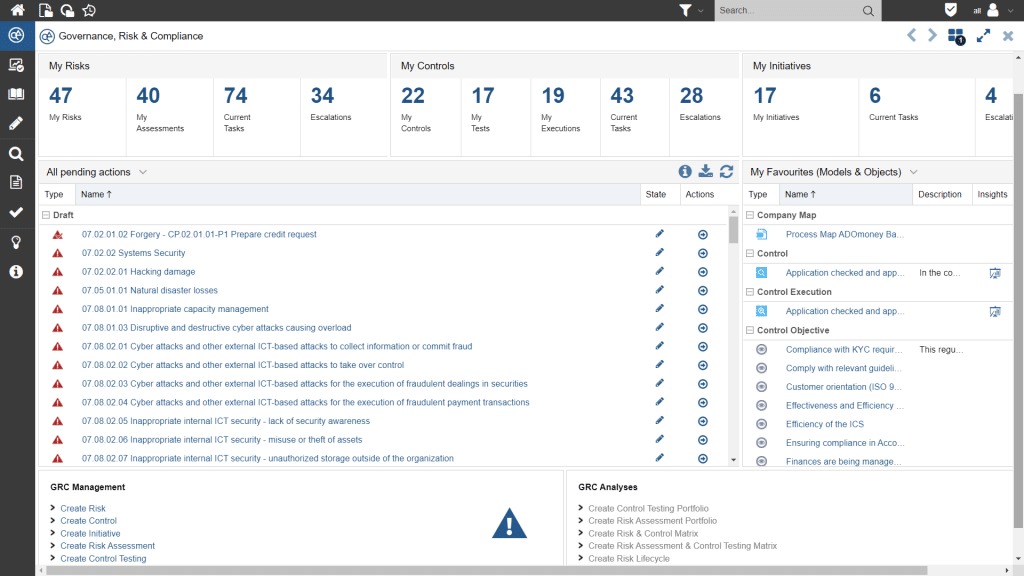
Figure 9: GRC workstation or GRC dashboard
Increase the efficiency of your security management
The consistent, end-to-end use of an integrated management system creates a repository that provides stakeholders in all management domains with previously unimagined insights and contributes to effective control as well as goal achievement. This is only made possible by the unified, continuous and decentralized assessment. The uniform and structured structure of security management at the levels of governance, strategy and operational implementation allows tasks to be clearly defined and assigned. The consistent use of an IT system at both strategic and operational levels enables the efficient, decentralized fulfillment of tasks. By using the process map as a basis, all relevant assets can be identified directly and the reference to the other governance systems can be established.